White Hat Hacker: Define, How to Become, and Career Paths
White hat hackers are the unsung heroes of cybersecurity, using their skills to protect systems from malicious attacks. This guide will define the role of a White Hat Hacker, outline the steps to become one, and explore the diverse career options available in this growing field.
Additionally, we will also name a few famous White Hat Hackers in the information technology world that you may also know about!
What is White Hat Hacker?

A White Hat Hacker, also known as an ethical hacker, is a computer security expert who specializes in testing and improving the security of computer systems and networks. They use their skills to identify vulnerabilities and weaknesses in these systems.
Unlike malicious hackers (Black Hats), they do so with the permission and cooperation of the system's owner.
Key Characteristics of White Hat Hackers:
Ethical: White Hat Hackers operate within the bounds of the law and adhere to a strict code of ethics.
Skilled: They possess a deep understanding of computer systems, networks, and security protocols.
Problem Solvers: Their primary goal is to find and fix security flaws, not to exploit them for personal gain or to cause harm.
Proactive: They actively search for vulnerabilities before malicious hackers can discover and exploit them.
Trusted: Organizations hire White Hat Hackers to assess their security posture and recommend improvements.
It's important to note that not all hackers with good intentions are White Hats. Grey Hat Hackers, for example, might hack systems without permission but with the intention of helping the organization. However, their actions are still illegal and can have serious consequences.
White Hat Hacker vs. Gray Hat Hacker vs. Black Hat Hacker

Before going into detailed explanations, let's break down the differences between white hat, gray hat, and black hat hackers:
White Hat Hackers (Ethical Hackers)
Motivation: They work to improve security systems by finding vulnerabilities before malicious hackers do.
Legality: They operate with permission from the owners of the systems they test.
Methods: They use the same tools and techniques as black hat hackers but for ethical purposes.
Employment: Often employed by security firms, government agencies, or as part of a company's internal security team.
Examples of Activities: Penetration testing, vulnerability assessments, security audits, and bug bounty programs.
Gray Hat Hackers
Motivation: A blend of both ethical and unethical motivations. They may find vulnerabilities without permission but disclose them to the owners, sometimes seeking a reward or recognition.
Legality: Their actions often fall into a legal gray area. While they might not have malicious intent, they still violate terms of service or access systems without authorization.
Methods: Similar to both white and black hat hackers. They may publicly disclose vulnerabilities to pressure companies to fix them.
Employment: They can work independently or be employed by security firms, but their methods are not always sanctioned.
Examples of Activities: Finding vulnerabilities in systems and disclosing them publicly, sometimes offering to fix them for a fee.
Black Hat Hackers (Crackers)
Motivation: Driven by personal gain, financial profit, or malicious intent to disrupt or damage systems.
Legality: Their activities are illegal and unauthorized.
Methods: Exploit vulnerabilities for various purposes, including data theft, identity theft, ransomware attacks, and website defacement.
Employment: Operate independently or as part of organized cybercrime groups.
Examples of Activities: Creating and distributing malware, phishing scams, hacking into corporate networks, and stealing financial information.
TL;DR White vs. Gray vs. Black Hat Hacker
White Hat Hackers: "Good guys" who hack with permission to find and fix security flaws.
Black Hat Hackers: "Bad guys" who hack illegally for personal gain or malicious intent.
Gray Hat Hackers: Somewhere in between, they might hack without permission but often disclose vulnerabilities to help improve security.
The lines between these categories can be blurry, and some hackers may exhibit behaviors from multiple categories depending on the situation.
How To Study White Hat Hacker
Becoming a white hat hacker is a rewarding journey that involves a combination of technical skills, knowledge, and ethical commitment.
Here's a roadmap by SkillTrans to guide you on your path to becoming a white hat hacker:
Build a Strong Foundation
Computer science fundamentals and cybersecurity concepts are two important things to understand if you want to become a White Hat Hacker, specifically:
Computer Science Fundamentals: Gain a solid understanding of computer architecture, operating systems (especially Linux), networking protocols (TCP/IP), and programming languages like Python, Java, or C++.
Cybersecurity Concepts: Learn about encryption, authentication, access controls, firewalls, intrusion detection systems, and common vulnerabilities.
Learn Ethical Hacking Techniques

Learning is important, the necessary knowledge cannot be from a single source. Participating in online courses, practicing, and obtaining information security certificates will help make your path to becoming a White Hat Hacker clearer, specifically:
Online Courses & Platforms: Consider platforms like Cybrary, Udemy, Coursera, or SkillTrans. Look for courses on penetration testing, vulnerability assessment, web application security, and network security.
Certifications: Certifications like Certified Ethical Hacker (CEH), CompTIA Security+, or Offensive Security Certified Professional (OSCP) can validate your skills and enhance your credibility.
Hands-on Practice: Set up your own lab environment to practice hacking techniques in a safe and controlled space. TryHackMe and HackTheBox (Both are free, also, have premium options) offer great challenges for beginners.
Specialize in a Niche
Security expertise is essential, to ensure the security of the fields you wish to work in, consider gaining expertise in the following:
Web Application Security: Focus on identifying and exploiting vulnerabilities in web applications.
Network Security: Learn how to secure networks from unauthorized access and attacks.
Mobile Security: Specialize in securing mobile devices and applications.
Cloud Security: Understand the unique security challenges of cloud environments.
Stay Updated

Eftsure reports a rise in security attacks, with an 80% increase in new malicious software targeting Macs. The U.S., India, Japan, Taiwan, and Ukraine are the top five countries affected by these malware attacks.
Notably, 49% of non-point-of-sale malware was installed through malicious emails. In 2020, 61% of organizations experienced malware spreading among employees.
Trojans are the most prevalent malware on Windows systems, accounting for 64.31% of attacks, followed by viruses at 15.52%.
It can be seen that network security attacks do not stop but show signs of increasing, forcing White Hat Hackers to always update their knowledge:
Follow Cybersecurity News: Keep up with the latest threats, vulnerabilities, and security best practices.
Join Online Communities: Participate in forums, blogs, and social media groups to learn from and network with other white hat hackers.
Attend Conferences: Cybersecurity conferences offer valuable insights and networking opportunities.
Gain Experience
While learning knowledge from the sources we mentioned above, you can directly join companies to become familiar with security projects:
Internships: Look for internships in cybersecurity firms or IT departments to gain real-world experience.
Bug Bounty Programs: Participate in programs where you can get paid for finding vulnerabilities in software and websites.
Capture the Flag (CTF) Competitions: Test your skills against other hackers in a fun and competitive environment.
Important Considerations
Last but not least, once you have gained skills and experience, don't forget that as a White Hat Hacker you must adhere to the following:
Legality: Always obtain permission before testing any systems. Unauthorized hacking is illegal.
Ethics: Adhere to a strict code of ethics. Use your skills only for good and never for malicious purposes.
What is the Career Path for a White Hat Hacker
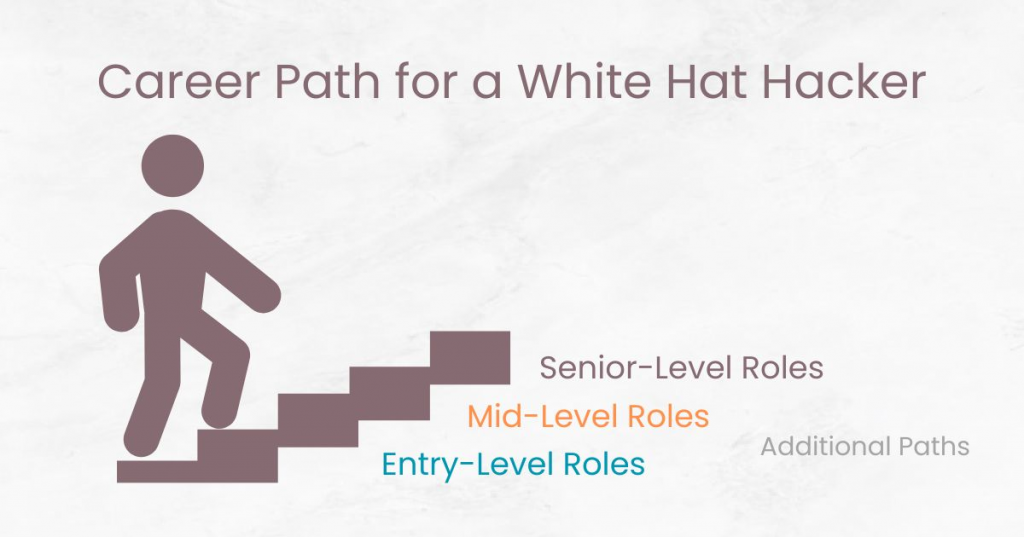
The career path for a white hat hacker, also known as an ethical hacker, can be diverse and fulfilling.
Here is a general outline of the potential trajectory a White Hat Hacker could take:
Entry-Level Roles
To gain more experience and become familiar with common security errors, White Hat Hackers can first target the following potential positions:
Information Security Analyst: Start by working in a security operations center (SOC), monitoring systems, analyzing logs, and responding to security incidents.
IT Auditor: Evaluate an organization's IT infrastructure to identify risks and ensure compliance with security policies.
Junior Penetration Tester: Work as part of a team to assess vulnerabilities in systems and applications.
Mid-Level Roles
Once more experienced, familiar with systems, and able to plan and handle system security issues, White Hat Hackers can target the following positions:
Security Engineer: Design, implement, and maintain security systems and solutions.
Penetration Tester: Conduct comprehensive security assessments, including vulnerability scanning, exploitation, and reporting.
Security Consultant: Advise organizations on security best practices and help them develop and implement security strategies.
Senior-Level Roles
White Hat Hacker endpoint, responsible for securing and preventing security risks for large systems or researching potential future security issues:
Security Architect: Design and build the overall security framework for an organization.
Chief Information Security Officer (CISO): Lead the organization's security strategy and ensure compliance with regulations.
Security Researcher: Specialize in vulnerability research, threat intelligence, or developing new security tools and technologies.
Additional Paths
In addition to the above positions, White Hat Hacker can also do many other jobs related to security expertise such as:
Bug Bounty Hunter: Earn rewards by finding and reporting vulnerabilities in company programs.
Security Trainer/Educator: Share your knowledge and expertise by training others in cybersecurity.
Entrepreneur: Start your own cybersecurity consulting firm or develop security products.
Famous White Hat Hackers
Here are some famous white hat hackers who have made significant contributions to the field of cybersecurity:
Kevin Mitnick

Kevin Mitnick, once dubbed the "world's most wanted hacker," has a legendary story that reads like a thrilling cyber-espionage novel.
In his youth, he gained notoriety for his audacious hacks into various computer systems, fueled by a combination of curiosity and a penchant for mischief. He infiltrated networks, manipulated phone systems, and even evaded law enforcement for years, making headlines around the world.
However, after a high-profile arrest and a five-year prison sentence, Mitnick emerged with a newfound perspective. He realized the potential impact of his skills and chose to redirect his expertise towards ethical pursuits. He became a "white hat" hacker, dedicating himself to helping organizations identify and address vulnerabilities in their security infrastructure.
Dan Kaminsky
Dan Kaminsky, a renowned security researcher, made a groundbreaking discovery in 2008 when he identified a critical vulnerability in the Domain Name System (DNS), the backbone of the internet's address system. This flaw, now known as the Kaminsky Bug, had the potential to wreak havoc on the internet, allowing attackers to redirect website traffic, intercept emails, and impersonate legitimate sites.
Understanding the gravity of the situation, Kaminsky quickly mobilized a coordinated effort with key figures in the DNS and security communities. He worked tirelessly, often in secret, to develop a patch that could mitigate the vulnerability before it could be widely exploited. This collaborative effort involved major software vendors, internet service providers, and government agencies.
Dan Kaminsky's discovery and leadership in addressing the DNS flaw solidified his reputation as a prominent figure in the cybersecurity world. His actions underscore the importance of responsible disclosure and the power of collaboration in safeguarding the Internet.
Steve Wozniak

Steve Wozniak, affectionately known as "Woz," is a legendary figure in the tech world, co-founding Apple Computer alongside Steve Jobs.
In his younger years, Wozniak was fascinated by electronics and communication systems. He became a self-taught "phone phreak," a term used to describe individuals who explored and manipulated the telephone network. Wozniak's mischievous curiosity led him to build "blue boxes," devices that allowed users to make free long-distance calls by replicating the tones used by telephone operators.
This early hacking experience laid the groundwork for Wozniak's later innovations. His understanding of electronics and communication protocols would prove crucial when he designed the Apple I and Apple II computers, which revolutionized the personal computing industry.
Jeff Moss
Jeff Moss, also known as Dark Tangent, is a prominent figure in the cybersecurity world. Black Hat, established by Jeff Moss in 1997, is a more corporate-focused event where security professionals discuss emerging threats, vulnerabilities, and solutions.
Moss's vision behind creating these conferences was to foster open communication and collaboration between the different players in the cybersecurity landscape.
Beyond the conferences, Moss has also served as a member of the U.S. Homeland Security Advisory Council and as the Chief Security Officer for ICANN, the Internet Corporation for Assigned Names and Numbers.
Charlie Miller

Charlie Miller is a highly respected security researcher and white hat hacker best known for his extensive work in uncovering vulnerabilities within Apple's ecosystem. Throughout his career, he has consistently pushed the boundaries of Apple's security, exposing critical flaws in both their Mac computers and iPhone devices.
His most notable accomplishments include being the first person to remotely hack an iPhone in 2007 by exploiting a vulnerability in its SMS processing. He also successfully compromised a MacBook Air in under two minutes at the Pwn2Own hacking competition in 2008.
Currently, Miller is a Principal Autonomous Vehicle Security Architect at Cruise Automation, where he focuses on securing self-driving cars from cyber threats. His dedication to exposing vulnerabilities and improving security measures continues to make him a prominent figure in the cybersecurity community.
Conclusion
In conclusion, White Hat Hackers are the unsung heroes of the digital age, working tirelessly to keep our information and systems secure. They represent a powerful force for good in the ongoing battle against cybercrime, and their contributions are essential for a resilient and trustworthy digital future.
If you want to become a White Hat Hacker, don't hesitate to start now. SkillTrans's security and cybersecurity online courses definitely help you on your path to becoming a White Hat Hacker!

Meet Hoang Duyen, an experienced SEO Specialist with a proven track record in driving organic growth and boosting online visibility. She has honed her skills in keyword research, on-page optimization, and technical SEO. Her expertise lies in crafting data-driven strategies that not only improve search engine rankings but also deliver tangible results for businesses.



