Computer Forensics: Definition, Roles, Processes & Example
The rapid growth of the global economy and information technology system is good news for people who want to improve and upgrade their lives. However, its downside also disrupts life, manifested by the constantly increasing crime situation in all fields. Those current issues force the birth of scientific disciplines that directly participate in cases, investigate the causes, and clarify the incident. One of the notable names is Computer Forensics. So what is Computer Forensics, and how is Computer Forensics applied? Let's explore Skilltrans right in the following article.
What is Computer Forensics?

In the 1980s, with the development of personal computers, when hardware theft, copyright infringement, data loss occurred, businesses and governments began to be more aware of security issues.
Computer Forensics, also known as digital investigation, is the work of detecting, protecting, and analyzing information stored, transmitted, or created by a computer or computer network. In order to make reasonable inferences to find the cause, explain the phenomena during the investigation process.
There are many different definitions of computer forensics. The following is the definition of Rodney Mckemmish – 1999: “Computer forensics is the process of identifying, preserving, analyzing and presenting digital evidence in a legally acceptable manner”.
Why do we need Forensics?
If you want to determine the cause of your website being attacked by which perpetrator and find an effective way to fix it, you will definitely need Forensics. In addition, Forensics also has the ability to identify the causes, incidents and provide further solutions. You can easily detect malware on your computer or check for abnormalities in the network, detect intrusions by strangers, etc. These are the advantages that users need Forensics.
The Goals of Computer Forensics
The goal of computer forensics extends beyond merely uncovering digital evidence; it aims to create a structured and legally compliant process for handling, analyzing, and presenting digital data in investigations.
Uncovering Truth in Digital Investigations
Computer forensics seeks to reveal the underlying truth in incidents involving digital systems. It traces the origin of cyberattacks, understanding the extent of a data breach, or determining whether digital evidence supports or contradicts claims in legal disputes.
Preserving Evidence with Integrity
Evidence integrity is paramount in computer forensics. The process takes place by creating exact forensic images of data, generating hash values, and documenting every step to ensure that the evidence remains unaltered. Any deviation could compromise the investigation or render the evidence inadmissible in court.
Supporting Legal Accountability
Computer forensics bridges the gap between technical findings and legal frameworks. To do this, forensic experts should interpret complex digital evidence in a clear and comprehensible manner.
Mitigating Risks and Strengthening Systems
Beyond reactive investigations, computer forensics plays a proactive role in preventing future incidents. Organizations analyze the causes and methodologies of cybercrimes to identify vulnerabilities, improve security measures, and develop strategies to mitigate risks.
Recovering and Preserving Information
Computer forensics have advanced techniques for recovering lost, deleted, or intentionally hidden information. It deals with encrypted files, uncovering malware traces, or piecing together fragmented data to reconstruct entire datasets.
Enabling Transparency and Accountability
In both criminal and corporate investigations, computer forensics provides the means to hold individuals or organizations accountable for their digital actions. Whether it's proving insider threats, identifying perpetrators of financial fraud, or tracking the origins of malicious software, forensics makes responsibility assigned accurately and fairly.
Adapting to Emerging Challenges
With the rapid evolution of technology, the field constantly adapts to new challenges, such as cloud computing, mobile device forensics, and encrypted communications. The goal is to remain one step ahead of perpetrators while upholding the highest standards of forensic science.
Edmond Locard's Exchange Principle for Computer Forensics
Edmond Locard (1877 - 1966) was known as the Sherlock Holmes of France. He was a forensic investigator and founder of the Institute of Criminology at the University of Lyon.
Edmond Locard's principle is that whenever two people come into contact with each other, something from one person will be exchanged with the other and vice versa. It can be skin cells, dust, or dirt, but this exchange happens - so we can catch the suspect.
With Computer Forensics, this principle is also completely true. When you work with a computer or an information system, all your actions will be rewritten (although finding the culprit in this case will be much more difficult and time-consuming).
The Roles of Computer Forensics
The expansion of the information technology industry, the usurpation of Big Data, the need for information security, and the complex situation of high-tech crimes, etc. have brought the need for information security to the forefront of many businesses and countries. It even strongly affects the survival of an organization because most of the agency's confidential and important information is authenticated in digital form.
To make it easier, you can imagine. If the state of the business's website is permanently stolen for unknown reasons by online economic crimes, the business is returned to a blank website. There is no use value, the total damage cannot be converted into money but into the loss of reputation and brand.
That is why all businesses, especially those operating on the information technology platform, have a technical team. These developers are responsible for designing the interface, fixing software errors. They also have the function of detecting and handling harmful agents to the website, restoring lost data, and setting up a firewall to ensure the safety of the business situation of the business.
The most typical illustration to talk about the important role of Computer science is to clarify the cause of the bankruptcy of the American energy corporation Enron in December 2024. It led to hundreds of employees losing their jobs.
If you are using a computer, just open a file and operate on that file, all your operations will be recorded. Many countries in criminal investigations have allowed the use of evidence extracted from the analysis process based on computer forensics.
However, the tools and functions of the industry must be constantly updated because when the computer system becomes more complex, this evidence can easily be hacked and deleted or changed by programs called anti-forensics. This action is similar to the act of criminals, in reality, creating fake crime scenes to prevent the investigation force from finding the culprit or answering roundabout, not true in mind, or deliberately denying the crime.
Processes of Computer Forensics
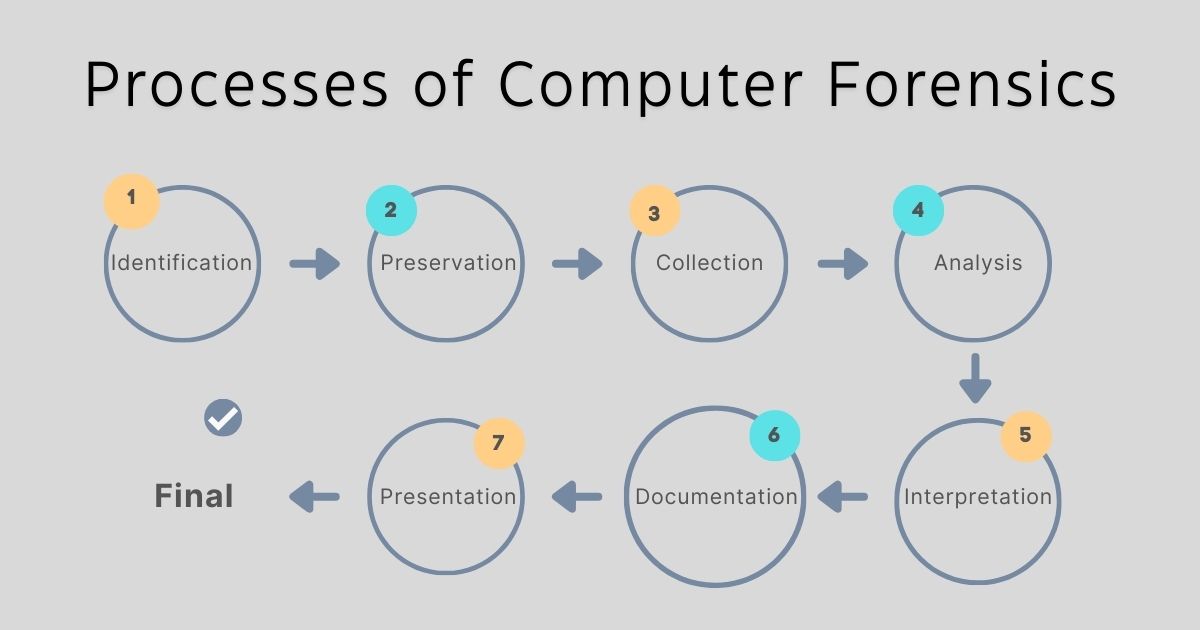
The processes of computer forensics form the foundation for successful investigations, preserving the integrity of the evidence and enabling its effective use in legal or organizational contexts.
Step 1: Identification
The first step is identification, investigators locate potential digital evidence across devices and systems. They determine what data is relevant, such as files, emails, system logs, or metadata. Sources of evidence can range from personal computers and mobile devices to servers, cloud storage, and external drives. Proper identification is a good start for all critical data.
Step 2: Preservation
Once identified, the evidence must be preserved to maintain its original state. A popular way is creating forensic images, which are exact copies of the data. Investigators document a clear chain of custody to track who has accessed the evidence and when, and apply cryptographic hashes to confirm the integrity of the data throughout the process.
Step 3: Collection
Next is the collection phase. Investigators use specialized tools to retrieve visible, deleted, or hidden information, including encrypted content. This process minimizes disruption to operational systems and creates a comprehensive data acquisition for analysis.
Step 4: Analysis
The raw data is examined to uncover evidence, patterns, or anomalies. Investigators recover deleted files, decrypt information, trace user activities, and analyze system logs. They may also reconstruct timelines and digital events to gain a clearer understanding of what occurred, identifying potential malicious activities or breaches.
Step 5: Interpretation
Investigators correlate digital evidence with other facts to build a coherent narrative, determining the relevance and implications of the discovered information within the broader investigation.
Step 6: Documentation
These reports must be precise and reproducible. This step is for the purpose of providing an accurate account of the investigation for both technical and non-technical audiences.
Step 7: Presentation
Finally, prepare comprehensive reports and, when necessary, get help from expert testimony to explain complex technical findings in a clear and understandable way. The presentation must adhere to legal standards the evidence must withstand scrutiny in court or other forums.
Characteristics of Computer Forensics
The field of computer forensics has several characteristics that set it apart from other investigative disciplines.
Scientific Approach
Computer forensics relies on a systematic and scientific methodology to collect, analyze, and present digital evidence. Every step is carefully documented for reproducibility as well as meet legal standards of reliability.
Legal Admissibility
Evidence handled in computer forensics must be admissible in court. Investigators strictly adhere to procedures such as chain of custody, preservation of evidence integrity, and compliance with legal standards or regulations.
Integrity and Authenticity
Maintaining the integrity of the original data is crucial. Techniques recommended are forensic imaging and cryptographic hashing so that evidence remains unaltered. It makes sure authenticity can be verified at any stage of the investigation.
Non-Destructive Process
The process avoids altering or damaging the original evidence. Investigators work on copies of the data (forensic images) to preserve the original source for future verification or examination.
Multidisciplinary Nature
Computer forensics combines expertise in technology, cybersecurity, legal frameworks, and investigative methods. Professionals must understand both the technical aspects of digital systems and the legal, procedural requirements of evidence handling.
Comprehensive Documentation
Every step in the forensic process is documented meticulously. This documentation validates the investigation and presenting evidence in legal or corporate settings.
Recoverability
Computer forensics specializes in retrieving deleted, hidden, or encrypted data. It employs advanced tools and techniques to recover lost information, making it a powerful tool for uncovering concealed evidence.
Timeliness and Accuracy
Investigations are conducted with precision and speed to meet deadlines in legal or organizational contexts. Forensic processes must balance thoroughness with efficiency to deliver actionable results without unnecessary delays.
Adaptability
The field addresses emerging challenges posed by new technologies, such as cloud computing, mobile devices, and encryption methods. Forensic experts must adapt their tools and techniques to remain effective in this dynamic environment.
Objectivity
Computer forensics is rooted in neutrality and objectivity. Investigators must present findings based solely on the evidence, without bias or interpretation that could compromise its credibility.
Tools and Techniques of Computer Forensics
Computer forensics tools and techniques cater to various aspects of investigations, such as data recovery, malware analysis, and network monitoring.
Forensic Imaging Tools
Forensic imaging tools create exact copies of digital storage devices. These tools capture bit-by-bit images, preserving every detail, including deleted files and hidden data. Popular tools like FTK Imager, EnCase, and Linux’s dd utility are widely used to perform this task securely.
Data Recovery Tools
Some typical data recovery tool names are R-Studio and Recuva. By them, investigators retrieve formatted, corrupted, or erased files from storage devices. They uncover concealed information that might otherwise remain inaccessible.
Network Forensics Tools
Network forensic tools analyze network traffic to detect anomalies, unauthorized access, or data exfiltration. Forensic experts usually use Wireshark and NetworkMiner to review packets in real time, helping trace the source and nature of malicious activities.
Memory Forensics Tools
Examining volatile memory (RAM) for uncovering running processes, malware, or user activity at a specific moment. Outstanding tools such as Volatility Framework, Redline extract and analyze memory dumps, revealing insights that are not stored on disk.
Malware Analysis Tools
Understanding malicious software and its impact requires specialized tools for malware analysis. IDA Pro, OllyDbg, and Cuckoo Sandbox support dissecting malware code, studying its behavior, and assessing its intent. These tools have a mission of combating cyberattacks and preventing future intrusions.
Techniques in Computer Forensics
In addition to tools, computer forensics employs various techniques to process digital evidence. Forensic imaging makes original data preserved, while timeline analysis reconstructs the sequence of events using timestamps from files and logs. Reverse engineering is used to understand software or malware, and steganography detection uncovers hidden data within media files. Each technique is carefully chosen based on the investigation's objectives.
Challenges of Computer Forensics

Computer forensics faces numerous challenges due to the dynamic nature of technology and the increasing sophistication of cybercriminals. These challenges range from technical and legal difficulties to resource limitations, all of which can hinder the effectiveness of investigations.
Rapid Technological Evolution
The constant development of new technologies, such as cloud computing, mobile devices, and Internet of Things (IoT) devices, presents a significant challenge. Investigators must continuously update their knowledge and tools to handle diverse, emerging platforms effectively.
Encryption and Data Obfuscation
Encryption is a double-edged sword, protecting user privacy while complicating forensic investigations. Advanced encryption methods or obfuscation techniques can render data inaccessible, delaying investigations and requiring specialized expertise with tools to decrypt or bypass protections.
Volume and Complexity of Data
Modern digital environments generate vast amounts of data, making it difficult for investigators to locate and analyze relevant evidence. The complexity of storage systems, such as distributed databases and cloud storage, adds further challenges in identifying, accessing, preserving evidence.
Lack of Standardized Procedures
The absence of universal standards for digital evidence handling and analysis causes inconsistencies in forensic processes. Different jurisdictions may have varying requirements, complicating cross-border investigations and the admissibility of evidence in legal proceedings.
Chain-of-Custody Issues
Maintaining a secure and well-documented chain of custody to create the integrity of evidence. Any lapse in tracking who accessed the evidence and when can compromise its credibility.
Resource and Expertise Limitations
Computer forensics needs specialized tools, infrastructure, and trained professionals. Smaller organizations or law enforcement agencies may face resource constraints, limiting their ability to conduct thorough investigations or adopt the latest forensic technologies.
Legal and Jurisdictional Complexities
Investigations often span multiple jurisdictions, each with its own legal frameworks and data protection laws. Navigating these laws can be challenging, especially when attempting to acquire evidence stored in other countries or subject to stringent privacy regulations.
Anti-Forensic Techniques
Cybercriminals increasingly use anti-forensic techniques, such as data wiping, steganography, and file encryption, to hinder investigations. These methods destroy, hide, or manipulate evidence, making it more difficult to trace their activities.
Volatility of Evidence
Digital evidence is inherently volatile, as it can be altered, deleted, or lost with ease. Investigators must act swiftly to secure evidence before it is compromised. It is difficult in live environments or when dealing with systems in active use.
Future Trends of Computer Forensics

Future trends in the computer forensics field are shaped by the growing complexity of digital environments, the increasing sophistication of cybercrime, and advancements in forensic tools and methodologies.
Artificial Intelligence and Machine Learning
AI and machine learning automate the analysis of large datasets and identify patterns or anomalies that may indicate malicious activities. These technologies can accelerate investigations, reduce human error, and provide deeper insights into complex cases.
Cloud Forensics
Future trends are developing tools and methods to acquire, analyze cloud-based evidence. It navigates challenges like multi-tenancy, encryption, and jurisdictional boundaries.
IoT Forensics
The increasing use of Internet of Things (IoT) devices introduces a new dimension to forensic investigations. These devices generate vast amounts of data that can serve as evidence in cases of smart homes, wearable technology, and connected vehicles. Its expansion also poses problems with new specialized techniques and tools to extract, interpret data from IoT ecosystems.
Blockchain Forensics
As blockchain technology becomes more prevalent in applications, forensic investigators must develop methods to analyze blockchain transactions and smart contracts.
Advanced Encryption and Privacy Challenges
Future encryption technologies and privacy-focused tools will make accessing evidence more difficult. Forensic techniques will need to evolve to decrypt or analyze data without compromising user privacy or violating legal boundaries.
Mobile and Wearable Device Forensics
The ubiquity of smartphones and wearable devices will hold an irreplaceable role in forensic investigations. Future developments will enhance tools for extracting and analyzing data from these devices, even in cases involving locked, damaged, or encrypted devices.
Big Data and Real-Time Analytics
As digital investigations deal with increasingly large datasets, big data analytics will become a determined element for processing and analyzing evidence efficiently. Real-time analytics support investigators to monitor ongoing incidents, such as cyberattacks, and respond proactively.
Quantum Computing and Post-Quantum Cryptography
Quantum computing poses a dual challenge for computer forensics: it is a component rapid decryption of current encryption standards, and introducing new quantum-resistant cryptographic techniques. Forensic tools will need to adapt to both exploit and counteract these advancements.
Cybersecurity Integration
The convergence of computer forensics and cybersecurity will grow stronger. Forensics response incident and threat hunting. Organizations will increasingly rely on forensic insights to strengthen their security measures.
Automation and Remote Forensics
The future will see greater automation in forensic processes, reducing manual effort and improving efficiency. Remote forensics creates an environment for investigators to analyze systems and collect evidence without needing physical access.
Requirements for the Computer Forensics Industry
If forensics in medicine or mechanical criminal investigation using physical methods is difficult, forensics fighting against technology-savvy criminals is even often more difficult. To ensure the most effective investigation and information analysis process, computer forensic scientists need to meet the following requirements:
Ability to program in many languages
Working in this, you not only play the role of an investigator but also have to hold the situation of a senior programmer by using a variety of computer languages. The most popular ones such as Script languages: C, C++, Rube, Python, ...
Professional knowledge
Of course, computer forensics requires more than any other branch of Computer Science. In addition to being fully equipped with knowledge of computer science, you must be a person with practical experience, having a deep understanding of operating systems and system exploitation applications.
High professional level
Computer forensic experts are the ones who understand better than anyone else the rules related to electronic evidence and are able to process that evidence. At the same time, they must be able to recognize signs of information being swapped and use professional measures to prevent it.
In addition, for criminal and civil cases, computer forensics investigators must become witnesses in court like forensic experts in practice.
A Real Example of Computer Forensics
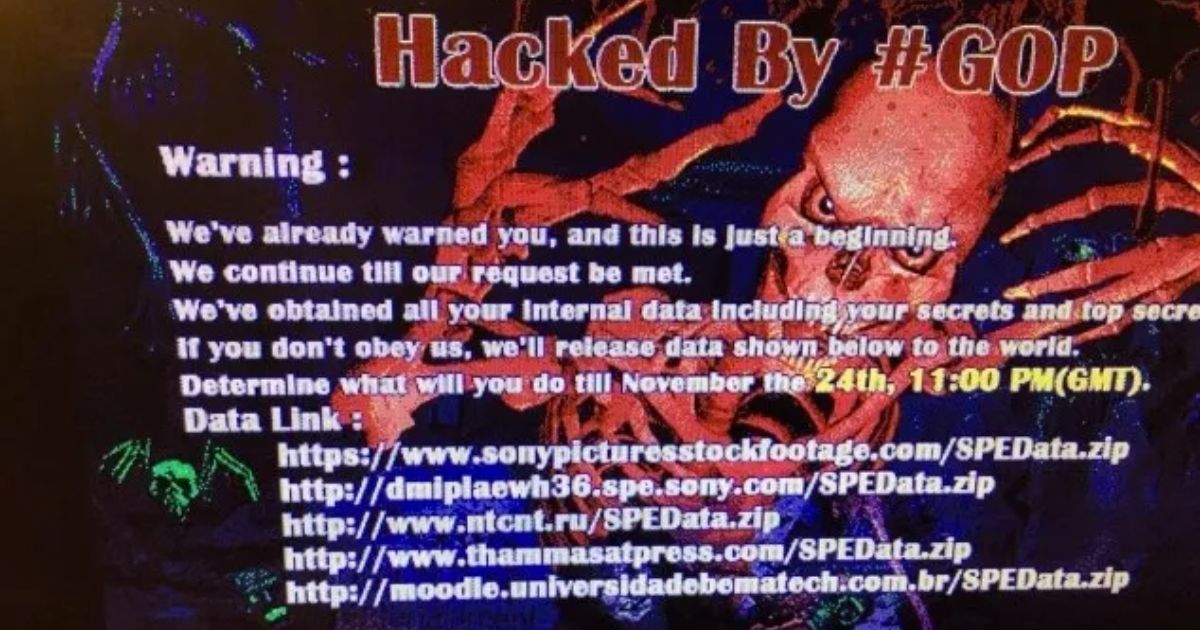
In November 2014, Sony Pictures Entertainment experienced a massive cyberattack. Hackers stole confidential data, including unreleased movies, sensitive employee information, and email correspondence. The attack was carried out by a group calling themselves the "Guardians of Peace" (GOP).
Role of Computer Forensics
Preservation of Evidence:
The computer forensics team secured the affected servers, workstations, and network logs to prevent tampering with the data. They created forensic copies of the compromised systems for analysis.
Malware Analysis:
Investigators examined malicious software used in the attack, identifying a type of malware designed to destroy data and exfiltrate information. The forensic analysis revealed links to other attacks attributed to North Korean hackers.
Log File Analysis:
Network activity logs were scrutinized to determine the timeline of the breach and how the attackers gained access.
Attribution:
Forensic findings pointed to specific IP addresses, malware coding styles, and attack patterns that matched those previously attributed to the North Korean "Lazarus Group." The U.S. government officially attributed the attack to North Korea.
Outcome
The forensic investigation helped Sony recover from the breach. It also provided critical intelligence for national security.
Currently, computer forensics is a fairly new field of study and is the brainchild of computer science. The average salary is up to 110,000 USD - the highest-paying industry in the US according to statistics from the University of Wisconsin. This is a great opportunity for computer science enthusiasts to combine their passion for criminal investigation to blossom their talents.
Your opportunities to work in this promising field can be expanded through Skilltrans courses. Some courses you can refer to (Please click on the course name below to learn more):
Genetic Algorithm Concepts and Working
This course helps you explore the principles of Evolutionary Computation and delve into Genetic Algorithms.
Artificial Intelligence for Humans - AI explained easy
You will learn:
The history of AI, and why this is the right moment to invest in it
How Machine Learning works, the set of techniques behind the AI revolution
How companies use AI to analyze images and build all sorts of products, from self-driving cars to unlock your iPhone with your face
How does the Internet work & Networking Crash Course
In this course, we will go on a journey together and we will look at all these concepts in a very visual way. You will see exactly how the Internet works. And from now on, when you make an operation on the internet, you will feel much more knowledgeable.
Conclusion
Hopefully, the above information about computer forensics and other interesting information about this industry will be really useful for you. The process of conquering your dream of becoming an expert in the field of high-tech investigation is not an easy journey. To do it, you can register for Skilltrans technology courses. Good luck!

Meet Hoang Duyen, an experienced SEO Specialist with a proven track record in driving organic growth and boosting online visibility. She has honed her skills in keyword research, on-page optimization, and technical SEO. Her expertise lies in crafting data-driven strategies that not only improve search engine rankings but also deliver tangible results for businesses.



